A major cybersecurity incident has come to light after a security researcher discovered an unprotected online database containing Stolen Login Credentials linked to millions of users worldwide.
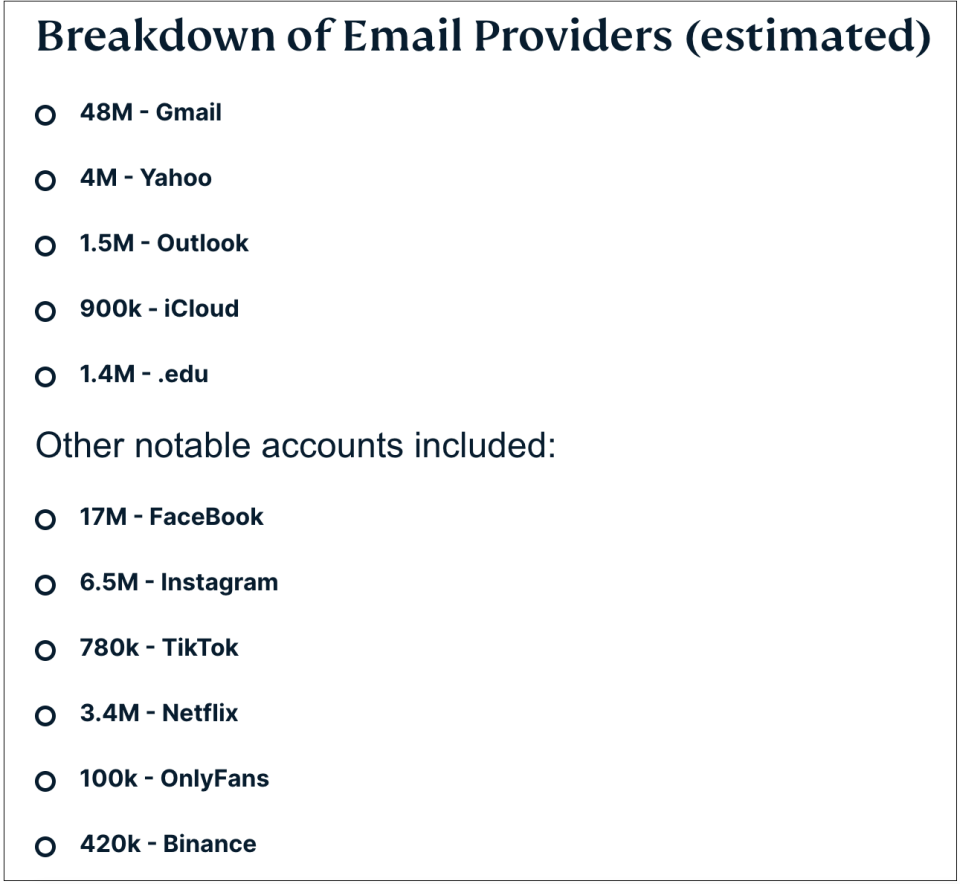
Jeremiah Fowler, a well-known cybersecurity researcher, found the database openly accessible on the internet with no password protection or encryption. According to Fowler, the exposed database contained 149,404,754 unique usernames and passwords, totaling nearly 96GB of raw data.
The leaked information included login details for popular platforms such as Gmail, Facebook, Instagram, Yahoo, and Netflix. Even more concerning, Fowler said the database also contained Stolen Login Credentials tied to financial services, online banking, credit cards, crypto wallets, and trading accounts.
Malware Likely Behind the Data Theft
Fowler believes the data was collected using malware known as information stealers. These malicious programs infect computers quietly and can steal saved passwords, capture keystrokes, or extract login data directly from browsers and apps. Victims are often unaware that their systems are compromised.
The database was neatly organized, allowing easy searches by victim name, platform, and account type. Fowler noted that while he was investigating, the number of records continued to grow, suggesting that the data was being actively updated with newly stolen information.
Who Owned the Database Remains Unknown
It is still unclear whether the database belonged to a cybercriminal group or a data collector researching compromised credentials. To reduce harm, Fowler contacted the hosting provider and requested immediate action. However, it took nearly a month and several follow-ups before the database was finally taken offline.

By the time it was removed, millions of Stolen Login Credentials had already been publicly accessible, leaving unknown parties able to copy the data.
Ongoing Risk Even After Takedown
Security experts warn that removing the database does not eliminate the threat. Shane Barney, Chief Information Security Officer at Keeper Security, explained that many Stolen Login Credentials remain valid long after they are stolen, allowing attackers to reuse them for fraud, identity theft, or further hacking attempts.
The database also reportedly contained login details linked to government (.gov) domains from multiple countries, raising serious national security concerns. Such access could be abused for spear-phishing, impersonation, or unauthorized access to government systems.
How Users Can Protect Themselves
Fowler advises users to take immediate steps to reduce their risk:
- Use reliable antivirus and anti-malware software
- Keep operating systems and apps fully updated
- Avoid downloading software from untrusted sources
- Change passwords regularly and never reuse them
- Enable two-factor authentication wherever possible
This incident highlights how widespread malware infections and poor password practices continue to put millions of users at risk, even when they are unaware their data has been compromised.